-
Sheldon Pinto
11:50 28th Jul, 2015
Lethal Android Texting Vulnerability Could Affect Millions Of Devices | TechTree.com
Lethal Android Texting Vulnerability Could Affect Millions Of Devices
Dubbed “Stagefright”, the vulnerability allows code to be executed without the need to open the message.

After the iOS text-messaging bug that was triggered by a string of unicode characters, comes another Android texting vulnerability that currently leaves millions of Android devices open to data theft and a lot more.
Zimperium Mobile Security has found out the new loophole that leaves millions of Android devices with outdated software vulnerable to attacks. The vulnerability is mainly a problem for older Android smartphones that have not been updated by manufacturers, even though Google has issued updates for the same.
The security issue comes from a piece of Android code (that is now named “Stagefright”). This code as the team member discovered, is frequently used to process, play and record multimedia files.
Upon receiving a video MMS, or even viewing video via a built-in web browser, the code will run the malicious code embedded in the video MMS, through its framework, thus giving access to core features and more to the hacker.
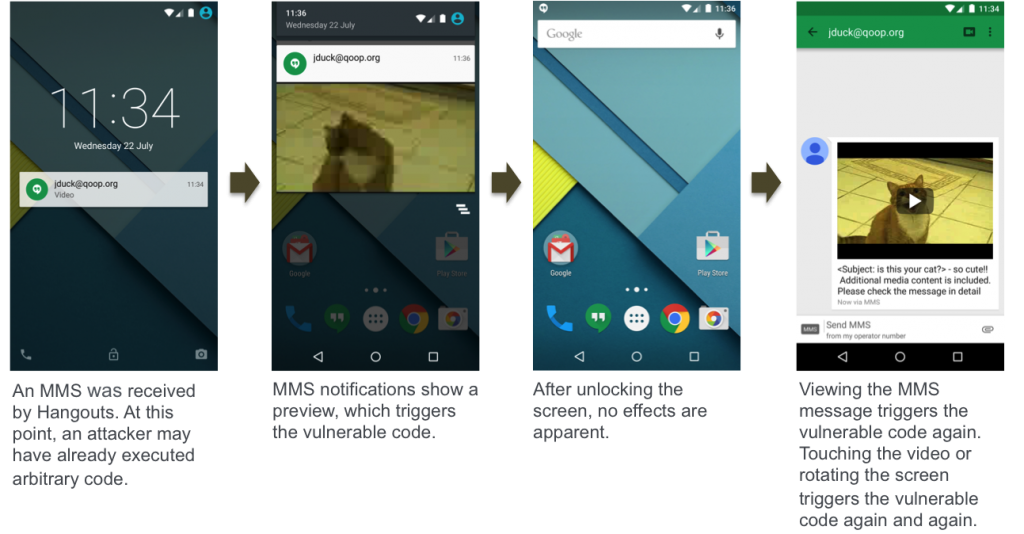
As the Zimperium has shown via the above screenshots, the user does not even need to open the MMS message with the bad code to execute it. Android’s notification system already does the job for you when you pull down the notifications shade, playing the downloaded video before you can take any action.
In some instances, the attacker may simply pull out the notification after it has been displayed and the user will not even know that his/her phone has been hacked into.
India becomes the perfect playground for such a vulnerability because local manufacturers rarely update software on devices once they have been sold.
Software updates are a problem for Android as custom skins and UIs designed by smartphone manufacturers often lead to a slower follow ups when it comes to firmware updates.
The Zimperium team has contacted Google for a patch and the search giant acted quickly to push out an update, but it clearly does not make much sense because the update would take months to reach Android smartphones with their custom UIs in the way.
TAGS: security flaw, Android
- DRIFE Begins Operations in Namma Bengaluru
- Sevenaire launches ‘NEPTUNE’ – 24W Portable Speaker with RGB LED Lights
- Inbase launches ‘Urban Q1 Pro’ TWS Earbuds with Smart Touch control in India
- Airtel announces Rs 6000 cashback on purchase of smartphones from leading brands
- 78% of Indians are saving to spend during the festive season and 72% will splurge on gadgets & electronics
- 5 Tips For Buying A TV This Festive Season
- Facebook launches its largest creator education program in India
- 5 educational tech toys for young and aspiring engineers
- Mid-range smartphones emerge as customer favourites this festive season, reveals Amazon survey
- COLORFUL Launches Onebot M24A1 AIO PC for Professionals







TECHTREE