-
Sponsored
11:19 31st Jan, 2022
Top 5 Biggest API Security Attacks in 2021 | TechTree.com
Top 5 Biggest API Security Attacks in 2021
As more than 80% of the internet's traffic runs through APIs, it is not surprising that hackers often try to find ways to exploit API security implications.

As more than 80% of the internet's traffic runs through APIs, it is not surprising that hackers often try to find ways to exploit API security implications.
2021 was the year of terrible breaches and data leaks on the internet as it witnessed different kinds of API abuse, including reverse engineering, unsecured database, session hacking, etc.
Let's look at the top 5 API security breaches and data leaks of 2021 that exposed the personal information of millions of people online.
1: Linkedin API Breach
What happened with Linkedin?
The Microsoft-owned LinkedIn has always been an invaluable target for cybercriminals. One threat actor, called "God User", in June 2021, was able to do the impossible when he scraped the data through LinkedIn APIs and posted information of 700 million LinkedIn users (more than 90% of total LinkedIn profiles) for sale on a Dark Web forum called RaidForums.
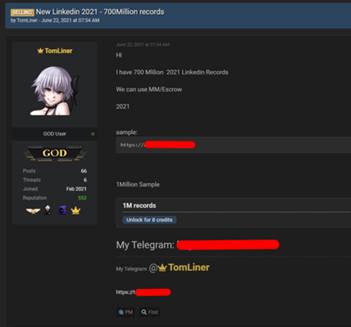
Image Source: inputmag
Impact: The leaked personal information fiasco was seen in the form of a sample of 1 million profile usernames and URLs, contact numbers, gender, inferred salaries, email addresses, social media account information, etc.
How did it happen?
The hacker explained that they had access to data due to querying LinkedIn’s servers. Users uploaded the accessed information to LinkedIn. However, LinkedIn APIs are not meant to serve as a login mechanism, and they cannot be used as such. This means they cannot be
utilized without prior authentication, making the attack post-login in nature.
Tips to Avoid: Risk-based protection for applications and APIs is vital to identify endpoints, their risk posture, and weaknesses.
WAAP (Web Application & API Protection) platform like AppTrana uses signature recognition, security-centric monitoring and Encryption as a Standard (TLS), and other security methodologies to block the attempt of API abuse.
2: NoxPlayer
In January 2021, a highly targeted cyber-attack on specific machines was discovered across Asia on NoxPlayer, the most popular Android games emulator, with over 150 million users, for Windows and MacOS.

Image Source: welivesecurity
Impact: Five NoxPlayer's users in Taiwan, Hong Kong, and Sri Lanka, who downloaded the update masquerading as a media player called NoxPlayer was infected with malware.
Cause: Hackers gained access to NoxPlayer's official API (api.bignox.com), and file-hosting servers (res06.bignox.com) exploits, and then it became a cakewalk for the perpetrators to change the software update download URL to send malware to Android emulator's victims in the Asian region.
Tips to Avoid: Make your web application more secure and avoid cyber hacks, malicious code, and unauthorized access by scanning your website/app at scale.
3: Bykea Data Breach
What happened?
Bykea, Pakistan's vehicle-for-hire and on-demand delivery app suffered a security breach of highly sensitive data related to its customers and drivers Personal Identifiable Information (PII), internal employee login credentials, and production server information and potentially lost its API logs.
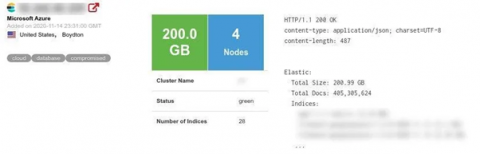
Impact: Over 400 million records comprising more than 200 gigabytes worth of data were exposed for weeks. The database server contained full trip information that was freely viewable by anyone. This also included where customers were picked up, dropped off, and when the drivers arrived during their trips.

Image Source: safetydetectives
Using business email addresses to publicly correspond with users could be potential inflection points that could serve as a gateway to an exploit by hackers who can utilize user data in any form and disguise it to take advantage of it.
Cause: The exposed elastic server instance was without password protection or encryption.
Tips to Avoid: The server should be encrypted, at rest and during transmission. Seeing the massive surge in cyber-attacks, leaving a database server accessible to the open internet without basic hygiene of encryption or authentication is like sending an open invitation to hackers.
Adopt security solutions that not only cover vulnerability assessments, security audits, and pen-tests, but also manage the security across your entire system.
4: The Central Bank of Russia' Money Heist'
What happened with the Central Bank of Russia API security breach?
According to banking officials, criminals could attack the bank's operations by intruding on its electronic inter-bank money transfer system. The threat actors could transfer funds from customer accounts through the Fast Payment System (FPS).
Impact: The 'money transfer' attack seemingly used to steal money from individuals, but no businesses have fallen victim.
How did it happen? A glorified case of broken object-level authorization, attackers, exploited enumerations, thanks to an API endpoint, to find a list of user accounts in the bank.
The hackers replaced the "Account ID" parameter with any random account number. The money theft was allowed to proceed, making it an unverified appearance as if that account had originated the request for funds to be transferred rather than the actual originating account.
Tips to Avoid: Restriction and total control on URL parameters need to sync with unique tokens. Safeguarding your cloud infrastructure from modern cyber-attacks, you're able to stop applications from being compromised effectively.
5: Parler API Breach
What happened with Parler?
An API security flaw enabled a white hat hacker, donk_enby, exploits a vulnerability in the Parler social media app. As a result, she was able to download archived public posts of users' data (including registration identifiers, emails, and timestamps for login activity) shortly before Amazon Web Services, Google and Apple terminated the Parler account and erased it off the internet.
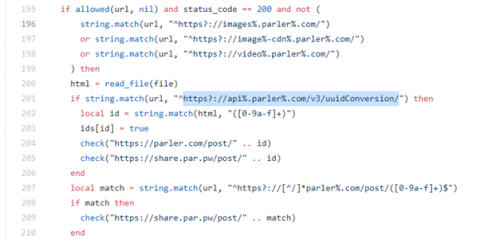
Image source: saltsecurity
Impact: 70 terabytes of data was stolen from the Parler social network by cybercriminals harvesting information through insecure APIs. Deleted and private posts, videos, images, drivers' licenses, geolocation, type of cell phones and IDs, etc., were part of the "archived" data.
How did it happen? A typical case of how to reverse engineer Parler's iOS API; the hacker used Ghidra software to explore and analyze the code of Parler to find public information. Interestingly, the social media app employed sequential numbering for post URLs, known as an insecure direct object reference, which was easy picking for the white hat hacker to understand the guessable pattern with API access to all post’s URLs without any authentication.
For example, https://yourapp(dot)folder/v1/photo?id= . Add 1, and you would end up getting the sequence of post URLs.
In Parler's case, one could guess the social media's post URL's chronological order (which is an ideal world, should be hidden and inaccessible) just by adding an incremented value of one.
Tips to Avoid: In an ideal world, URLs should be hidden and inaccessible, with limitations on public API calls. AppTrana, through its innovative positive security model and behaviour-based DDoS policies mitigates such attacks.
Conclusion:
The year 2022 thrives on the notion of effective security awareness, reinforcing API security best practices paves way for winning cyber security systems.
And Indusface WAF will not leave any stone unturned to keep your business safe and sound on the web.
TAGS: Sponsored
- DRIFE Begins Operations in Namma Bengaluru
- Sevenaire launches ‘NEPTUNE’ – 24W Portable Speaker with RGB LED Lights
- Inbase launches ‘Urban Q1 Pro’ TWS Earbuds with Smart Touch control in India
- Airtel announces Rs 6000 cashback on purchase of smartphones from leading brands
- 78% of Indians are saving to spend during the festive season and 72% will splurge on gadgets & electronics
- 5 Tips For Buying A TV This Festive Season
- Facebook launches its largest creator education program in India
- 5 educational tech toys for young and aspiring engineers
- Mid-range smartphones emerge as customer favourites this festive season, reveals Amazon survey
- COLORFUL Launches Onebot M24A1 AIO PC for Professionals







TECHTREE