-
Team TechTree
09:58 06th Mar, 2020
Browsers To Block HTTPS Sites Using Early TLS Versions | TechTree.com
Browsers To Block HTTPS Sites Using Early TLS Versions
Given the growing importance of privacy and data security, the step is one in the right direction as website owners would figure out

Millions of websites that use older version of Secure Socket Layer (SSL) and Transport Layer Security (TLS) protocols could find their websites getting knocked off from most browsers before end-March.
Given that enterprises aren’t prompt with updating even their SSL or TLS certificates on time, there could be a scenario where web properties belonging to major banks, government organizations, e-commerce stores and news organizations could go offline as browsers start replacing their early warnings with full-page error notes.
Secure Socket Layer and Transport Layer Security are two protocols used by websites to help guarantee your privacy and security. Some websites choose SSL, and some choose TLS. When security is being discussed, though, SSL is often used generically for both protocols. If you're concerned about the security of the information you give to a website, use your browser to find which version of SSL is being used.

A report published on the Netcraft.com says the older versions of the Transport Layer Security protocol, which date back to 1999 and 2006, are vulnerable to numerous practical attacks that have been resolved in later versions.
Back in 2018, the four largest browser vendors — Mozilla, Google, Apple, and Microsoft — jointly announced the deprecation of TLS 1.0 and 1.1, with support to be removed from their browsers in March 2020. But a number of notable sites have not heeded these warnings, and have so far failed to switch to a version of TLS more modern than 1.0, says the report.
In the run-up to the ultimate TLS 1.0 and 1.1 shut-off, many browsers have been presenting visitors to such sites with UI cues indicating the usage of these insecure protocols. Chrome 79, for instance, started using the words "Not Secure" in the address bar, and Firefox shows a yellow warning triangle.
The article, which questions the reasons websites aren’t upgrading their security protocols, says that Despite TLS 1.1 becoming a standard in 2006, and TLS 1.2 in 2008, they did not initially attract much attention, with many people at the time believing that the level of security provided by TLS 1.0 was simply good enough.
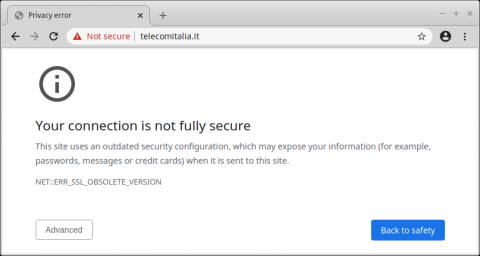
It wasn't until later when the flaws with SSL 3.0 and TLS 1.0 began to be fully realised that the web community began to push for adoption of TLS 1.1 and TLS 1.2. TLS 1.2 didn't gain widespread browser support until five and a half years after its standardisation, when Firefox 27 added support in 2014 — the last major browser to do so.
But operating systems and server software also took some time to catch on, and aren't as readily upgrade-able. Even today, end-of-life legacy systems, such as RHEL 5, Debian 6 (Squeeze), and Windows Server 2003, which never supported TLS 1.2, are still used on the web. Which is why removing client-side support for these older protocols is the most effective way of ensuring that their associated vulnerabilities can no longer pose any risks.
In case you want to check out the infrastructure and technology on which your website is running, do so by clicking here.
TAGS: Security, SSL, protocols, Browser, Chrome, Safari, Firefox
- DRIFE Begins Operations in Namma Bengaluru
- Sevenaire launches ‘NEPTUNE’ – 24W Portable Speaker with RGB LED Lights
- Inbase launches ‘Urban Q1 Pro’ TWS Earbuds with Smart Touch control in India
- Airtel announces Rs 6000 cashback on purchase of smartphones from leading brands
- 78% of Indians are saving to spend during the festive season and 72% will splurge on gadgets & electronics
- 5 Tips For Buying A TV This Festive Season
- Facebook launches its largest creator education program in India
- 5 educational tech toys for young and aspiring engineers
- Mid-range smartphones emerge as customer favourites this festive season, reveals Amazon survey
- COLORFUL Launches Onebot M24A1 AIO PC for Professionals







TECHTREE