-
Phalgunn Maharishi
15:46 17th May, 2017
All You Need To Know About WannaCry Ransomware | TechTree.com
All You Need To Know About WannaCry Ransomware
WannaCrypt0r has become one of the most virulent ransomware attack after the CoNFicker attack in 2008.
The date was May 12, and the whole world witnessed one of the most devastating ransomware attacks in the history of cyber security, the WannaCrypt0r 2.0, which infected more than 2,30,000 computers in over 150 countries. In-fact, popular companies like FedEx, LATAM Airlines and government agencies like Britain’s National Health Service were also hit by the ransomware attack. Also, it turned out that Russia and India are the two worst hit countries, because of extensive use of Windows XP.
Where did it originate from? How did it spread so fast?
WannaCry seems to have attacked computers in Russia first, after which the ransomware quickly spread to as much as 150 + countries and affected Microsoft computers. The ransomware is known to be using the age old technique of spamming and fishing to spread at such a fast pace. However, the malware seems to have also spread so fast due to a specially crafted worm that jumps from system to system in a network.
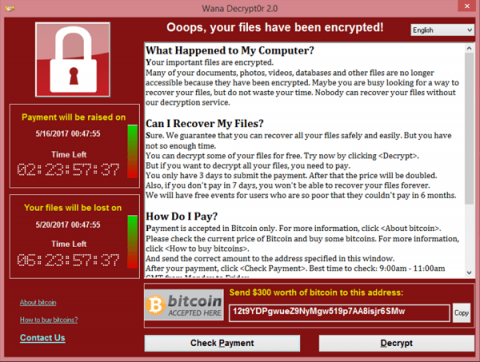
Which types of systems have been infected so far?
WannaCry is custom built for windows only. Linux, Mac or any unix based OS are not affected. The higher risk of being encrypted lies at those Microsoft computers that are not patched with the update. In-fact, to recall, Microsoft recently issued a patch for non-supported OS version such as Windows XP, Windows Server 2003, and Windows 8.
However, it seems that those with Windows XP are most largely hit by the ransomware. And, if you were guessing that Windows 10 wouldn’t catch this malware, you might be wrong. Windows 10 users can also be affected if they are not patched and updated.
Will ATMs, Banks, IT Companies be affected by this?
In short, banks, financial institutions, large enterprises, small enterprises - all will be hit, and there is no doubt about it. However, ATMs on the other hand run embedded XP, and SMB is mainly used for file sharing and thus, it may be safer when compared to other systems. Yet, we may never guarantee.
However, the biggest issue is the rampant use of pirated windows software, which will in-fact result in no patch maintenance, which further means, more havoc in the country.
How to safeguard from WannaCry?
- Use the latest Operating System.
- Make sure automatic updates are enabled, and downloaded regularly.
- Ensure Firewall is enabled to block all network based attacks.
- Disable SMB service completely if required.
- Never Click/Download anything on Emails from untrusted sources. Make sure the mail is from a trusted party, only then download the attachments.
- Use a proper, regularly updated Antivirus.
TAGS: WannaCry, Ransomware
- DRIFE Begins Operations in Namma Bengaluru
- Sevenaire launches ‘NEPTUNE’ – 24W Portable Speaker with RGB LED Lights
- Inbase launches ‘Urban Q1 Pro’ TWS Earbuds with Smart Touch control in India
- Airtel announces Rs 6000 cashback on purchase of smartphones from leading brands
- 78% of Indians are saving to spend during the festive season and 72% will splurge on gadgets & electronics
- 5 Tips For Buying A TV This Festive Season
- Facebook launches its largest creator education program in India
- 5 educational tech toys for young and aspiring engineers
- Mid-range smartphones emerge as customer favourites this festive season, reveals Amazon survey
- COLORFUL Launches Onebot M24A1 AIO PC for Professionals







TECHTREE